Configuring Okta Single Sign-On (SSO)
This guide will walk you through configuring the ngrok dashboard to use Okta as an identity provider and enable single sign-on for your ngrok account. This should not be confused with configuring an ngrok edge to allow your application users to log in using Okta.
The requirements for completing this guide are:
- Admin access to create new applications in Okta
- Admin access to edit your ngrok account settings
- An ngrok Enterprise account
Create a new SAML App Integration in Okta
- From the "Applications" menu, click the blue "Create App Integration" button.
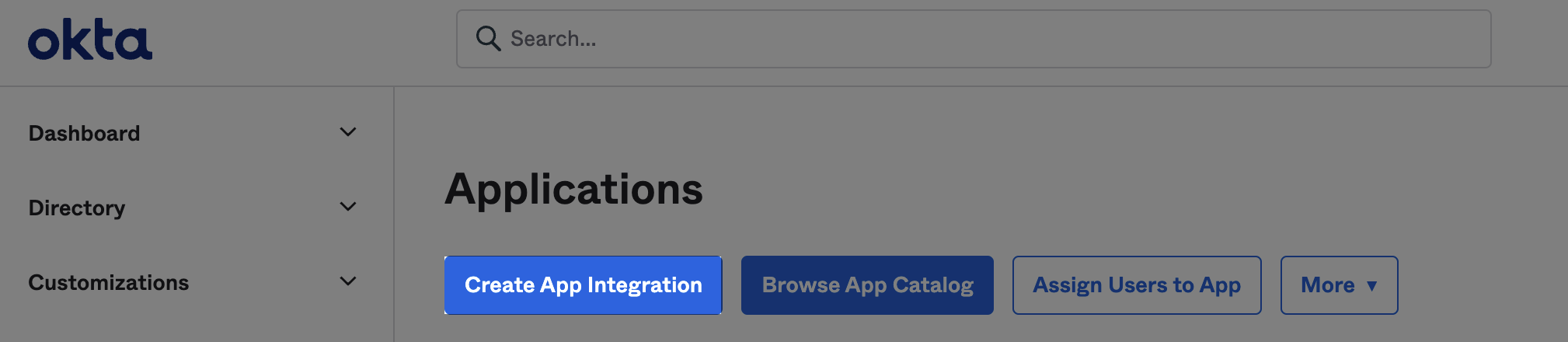
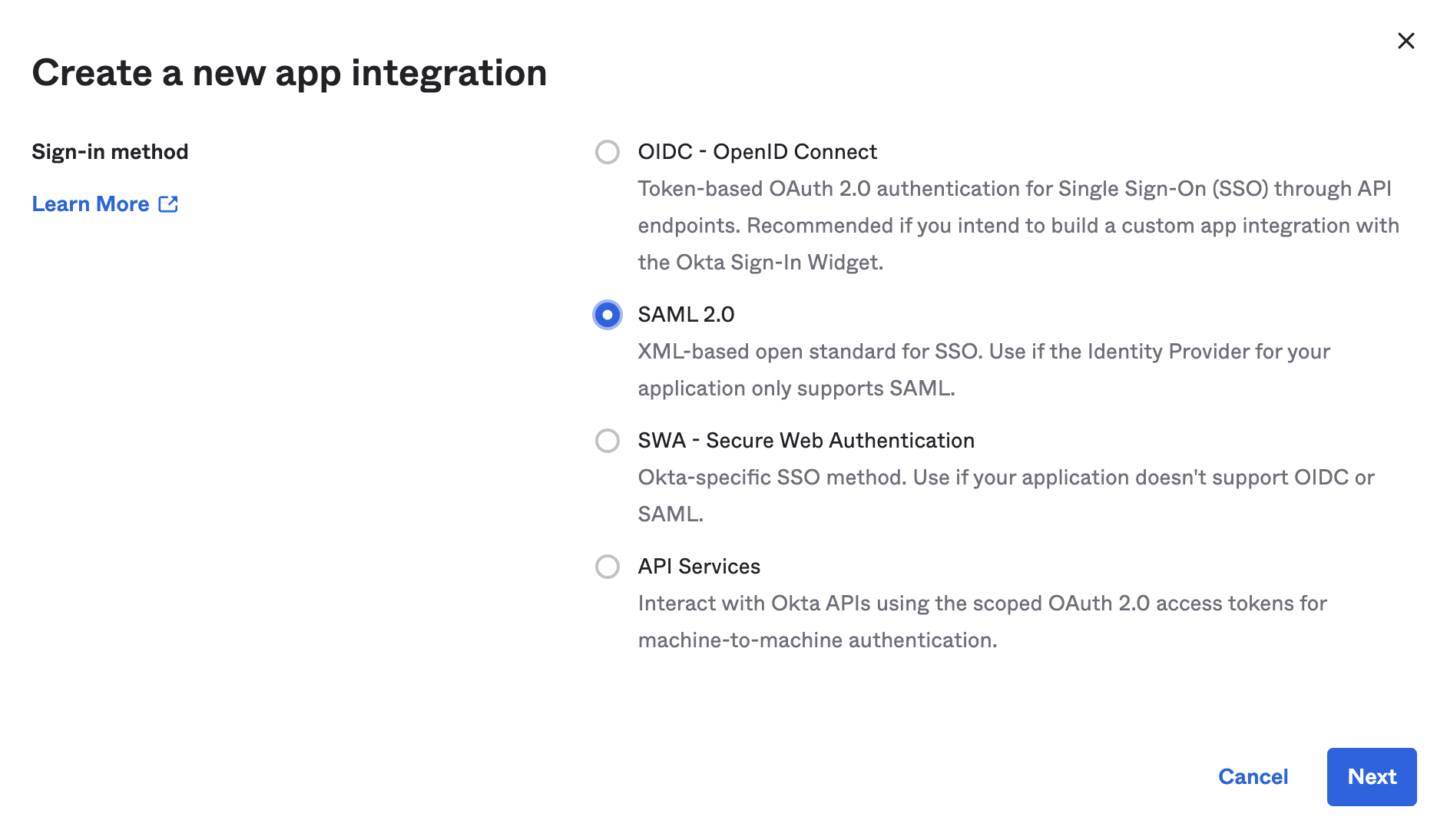
- Select "SAML 2.0" and click "Next"
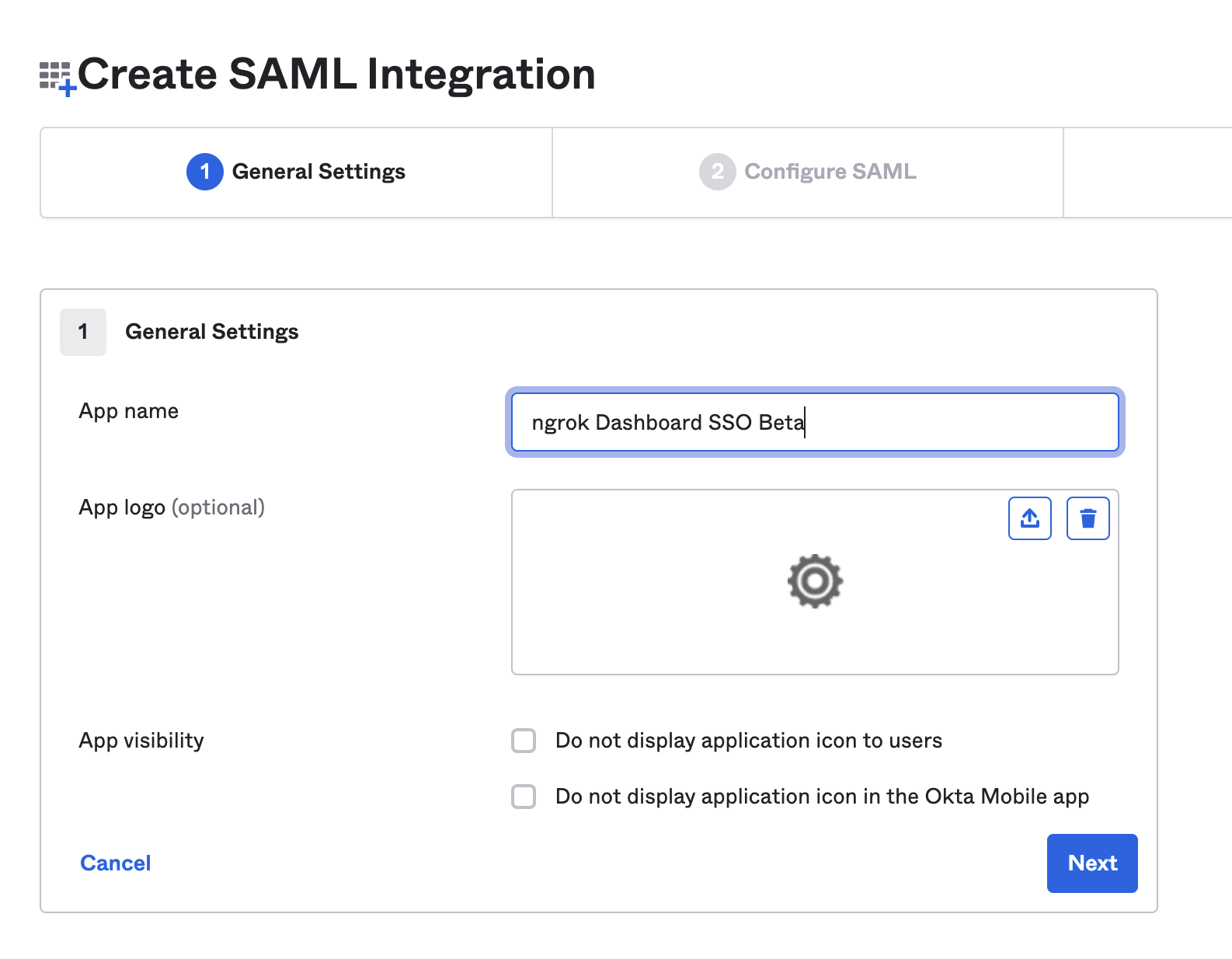
- Give your app a name, and click "Next"
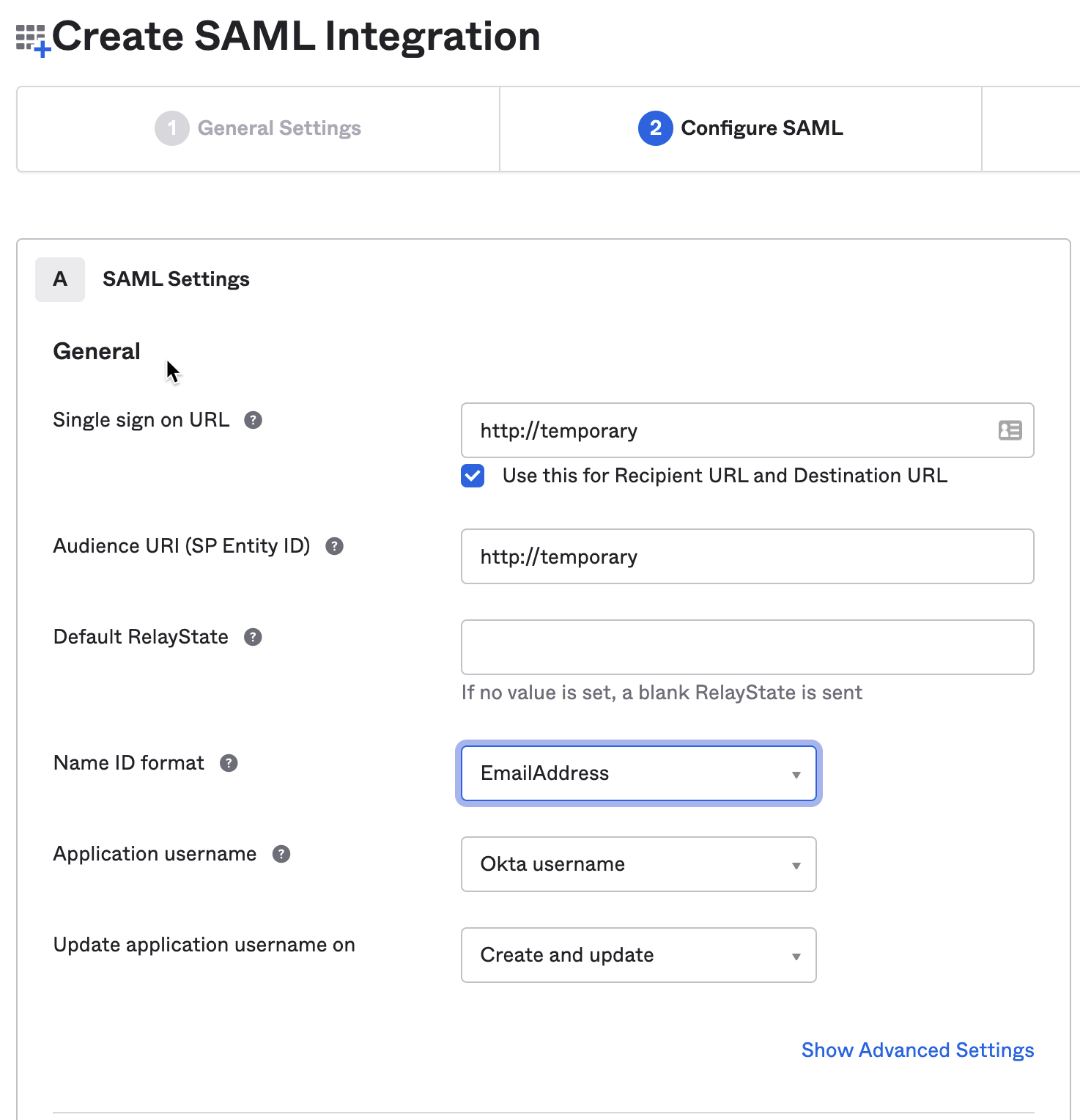
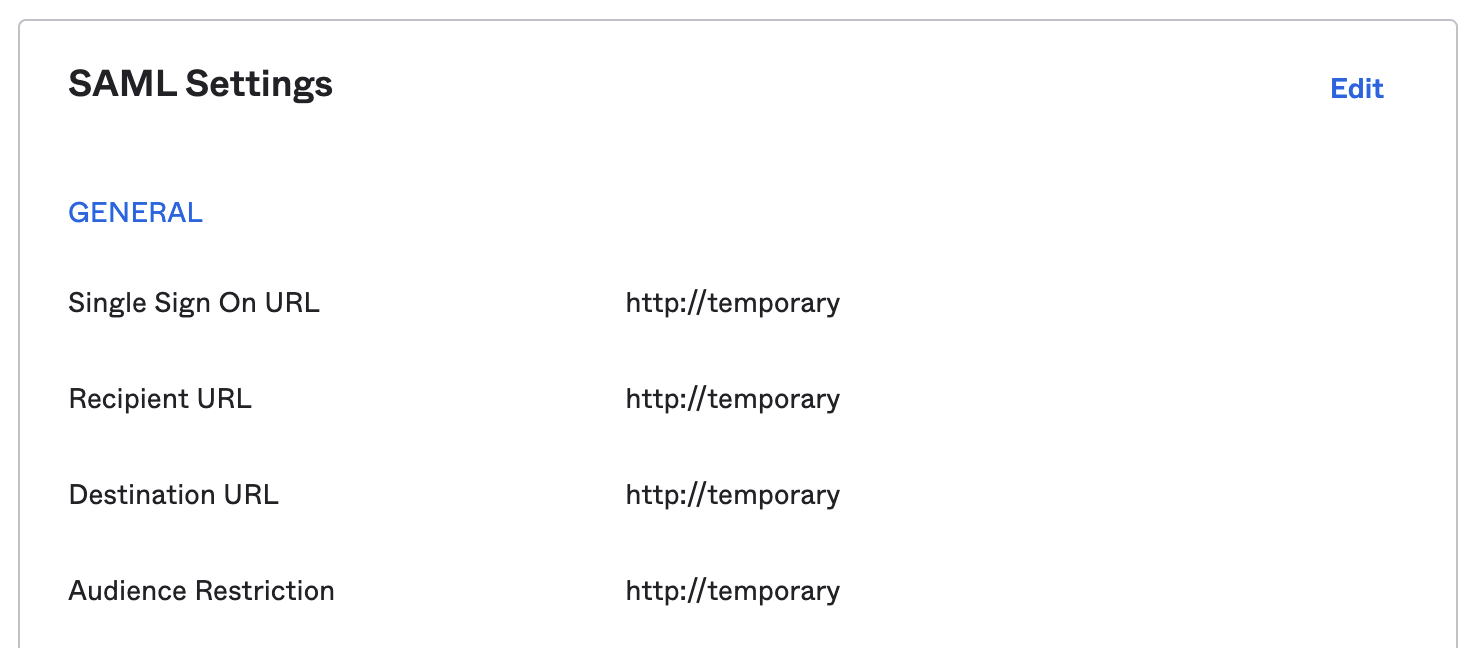
- Enter in temporary values for "Single sign on URL" and "Audience URI" and select "EmailAddress" for "Name ID format" and then click "Next". ngrok requires the username to be in email format.
- Select "This is an internal app that we have created" and click "Finish".
Download your SAML App metadata XML
- Navigate to the "Sign On" Tab on the new app and click on "Actions" under the Active SHA-2 certificate
- Click "View IdP metadata".
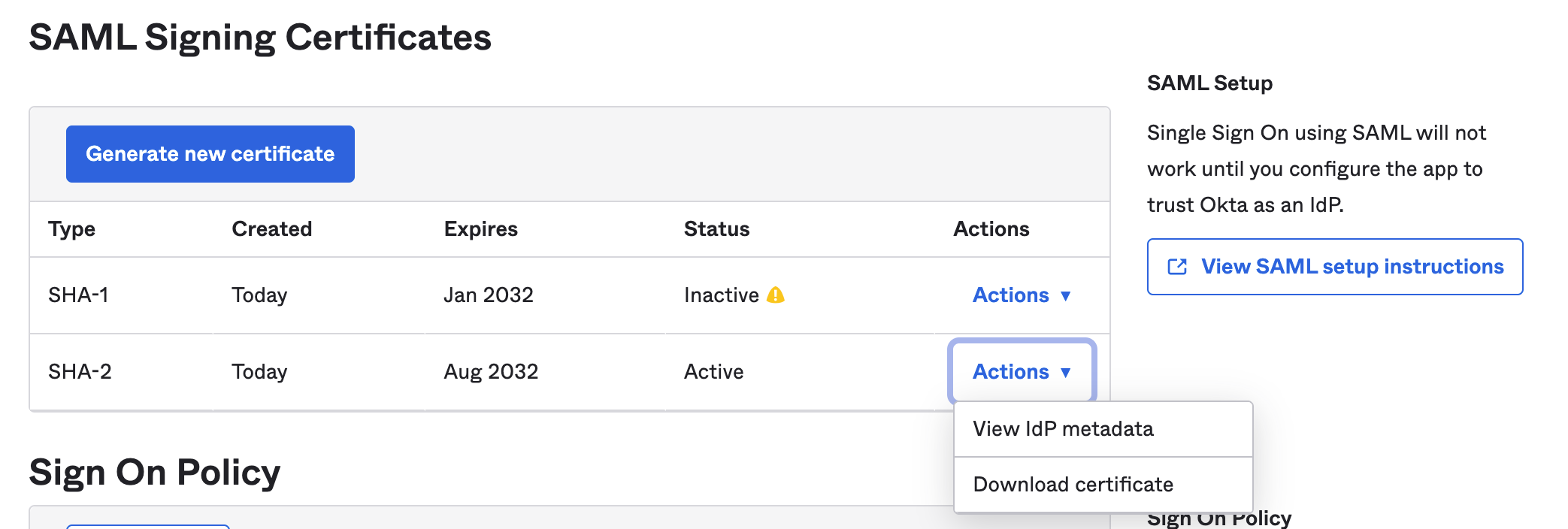
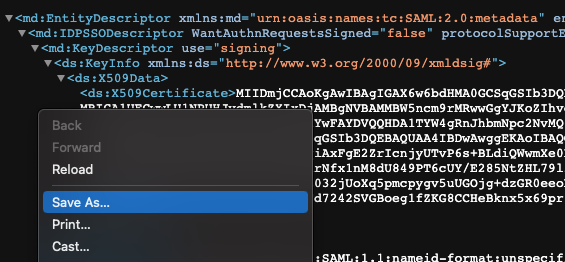
- In that new window, Select "Save As" from the File menu to save your metadata.xml file for uploading into ngrok in a later step.
Configure Single Sign-On (SSO) for your ngrok account
- Log into your ngrok dashboard and navigate to the "Settings > Account" section in the left navigation menu.
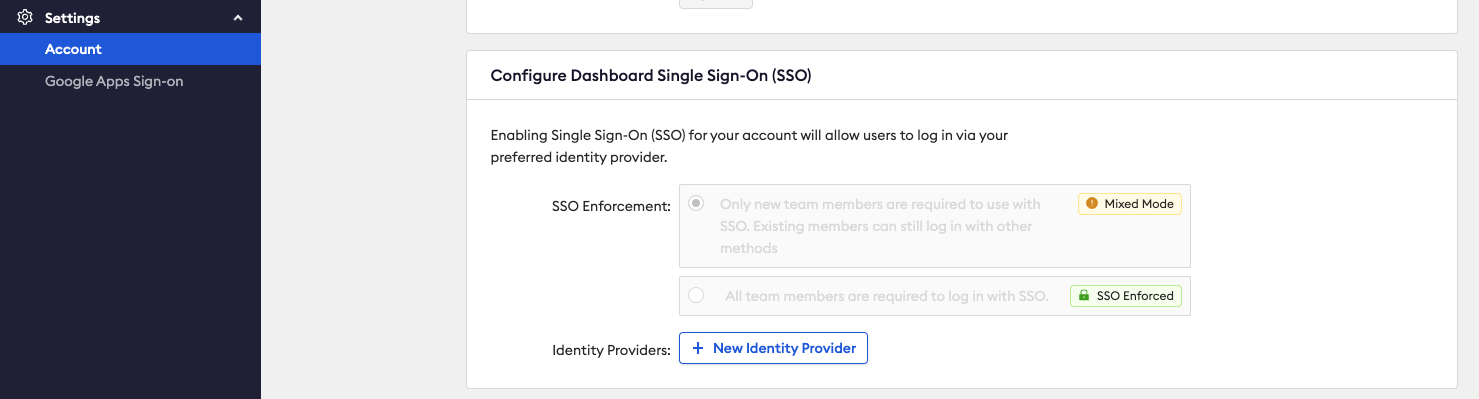
- Select "+ New Identity Provider" button to add a new identity provider.
- Add a helpful description, and then upload the metadata.xml file from Okta into the ngrok dashboard.
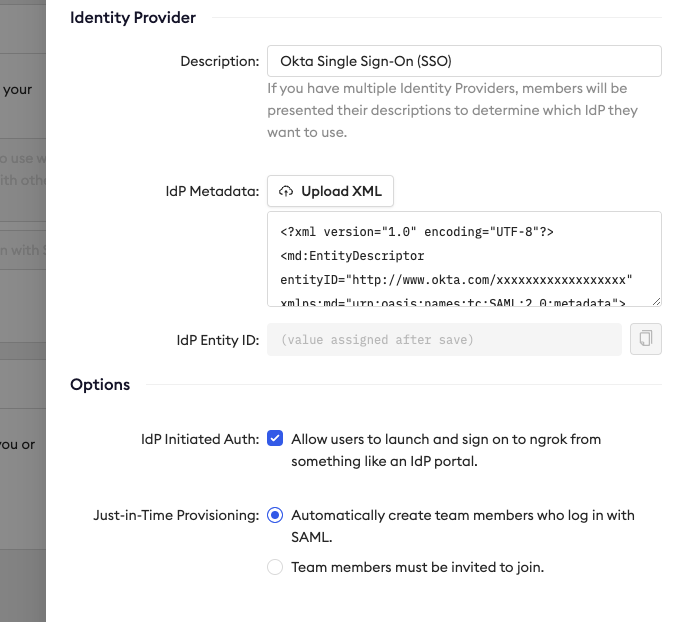
- In the Options section, select whether you'd like to allow users to log into the dashboard directly from their Okta dashboard
- Click "Save". Clicking Save will create the integration and generate the required URLs for your Okta Application.
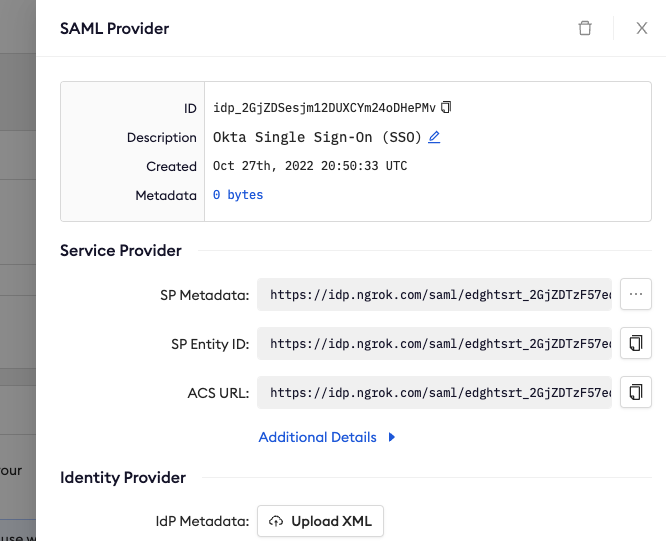
Add the ngrok generated URLs to your Okta SAML application
- Back in your Okta account, on the "General" tab of your Okta app, click on "Edit" under "SAML Settings"
- Click 'Next' on the 'General Settings' tab to get to the 'Configure SAML' tab.
- Replace the values ngrok provided you. Put the ngrok 'ACS URL' value into Okta's "Single sign on URL" field. Put the ngrok 'SP Entity ID' value into Okta's "Audience URI (SP Entity ID)" field.
- Click "Next". Click "Finish".
Congratulations, you should now be configured property to log into your ngrok account using Okta!
By default, your ngrok account will still allow users to log in with their existing credentials as well as through Okta ("Mixed Mode"). Once you verify that everything is working properly with your integration, you can enable "SSO Enforced" in the ngrok Dashboard which will require all new users to log in through Okta for their ngrok account.